
Information and document security is an increasing concern for the U.S. Federal government, both for internal systems and for systems operated by contractors or suppliers. Recently, the National Institute of Standards and Technology (NIST) published updated guidance to help organizations and agencies better protect against cyber attacks in the supply chain. The Biden administration made this a major focus of the cybersecurity executive order last year to prevent breaches like the attack involving the SolarWinds’ Orion product. This revised guidance is meant to encourage agencies to assess vulnerabilities not only of internally-developed systems and software but also of products and installed software created outside the United States. NIST’s Zero Trust framework is an important facet of evolving cyber investments and digital transformation within agencies, in addressing cyber vulnerabilities and mission risks.
Compromise of Controlled Unclassified Information (CUI) data may represent the path of least resistance for cyber attackers, and one of the most significant risks to our national security. CUI can be distributed by the government, for use by the Government Contractor (GovCon) community in opportunity assessment, program and technical analysis, and this CUI may include information and data that ultimately becomes part of program execution, requiring standard security controls. Examples include, but are not limited to:
- System technical details and locations
- Mission process and personnel role descriptions
- Information security needs or risks
- Data repository designs or schemas
- Access control and end-user device requirements
CUI and 3PAO Attestation
Do you accept and use CUI in your sales, capture, proposal and program transition activities? Is your CUI properly secured and protected, and how do you know?
Engagement of the GovCon community with Federal programs, systems, and communications is most secure with 3rd-party attestation (3PAO) of continual, certified protection of CUI. Self-certification is insufficient. This includes data shared among employees, vendors, and teaming partners participating in end-to-end opportunity pursuits and mission award transition.
Secure CUI With Capture2Proposal
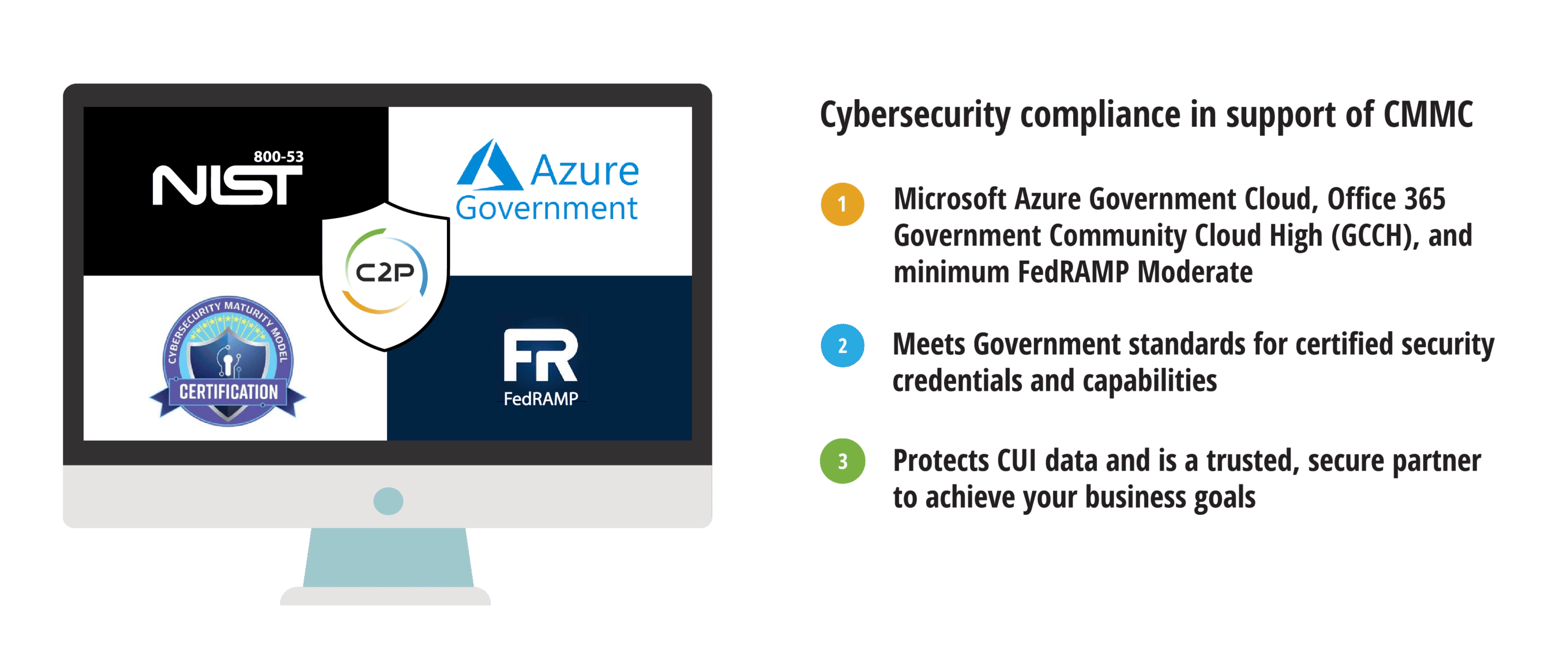
It is critical for GovCon organizations to understand CUI data characteristics and profiles, and how to manage and secure it. The Cybersecurity Maturity Model Certification (CMMC) program outlines requirements regarding how organizations contracting with the DoD must maintain their CUI.
Are you already aware of this risk, understand CMMC, and seeking a compliant software platform for managing your GovCon opportunity document lifecycle? C2P has recently received 3PAO attestation for CMMC v2.0 Level 2 compliance, which verifies information management security compliance with Federal Government-wide standards and controls as required by DFARS 252.204-7012. This includes use of FedRAMP-authorized cloud services via Microsoft’s Azure government cloud (Moderate, per NIST SP 800-53).
With C2P, organizations can store and share CUI and proprietary artifacts across the entire business development and proposal lifecycle, all while complying with CMMC regulations.
Very few software and cloud SaaS platforms used by the GovCon community at this time, outside of awarded contract work, fully protect CUI according to developing and constantly-changing DoD standards for CMMC.
No other platform for sales, CRM, capture and proposal management GovCon activities maintains this level of CUI protection.
Find out how C2P can help today!
